Skip to Content
- 主頁
- 關於
- 服務
- 常見問題
-
最新消息
- Phishing Alert: Are You Available?
- SPSS License Server Availability from 1 Jul
- MATLAB License Server Maintenance on 23 Jul
- APAN60 International Conference – Student Helper Recruitment (28 Jul – 1 August 2025@ Grand Hyatt Hong Kong)
- Elevate Your Cybersecurity Knowledge with IS Awareness Program
- 支援
 from Windows Program list and in the program bar
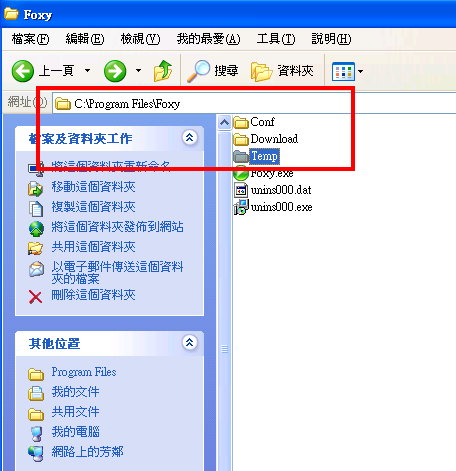
from Windows Program list and in the program bar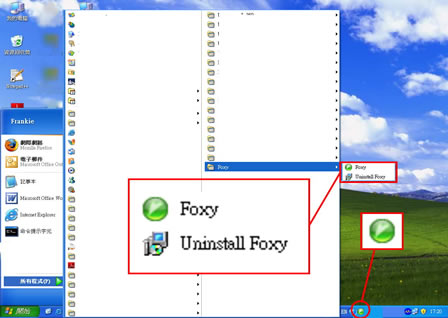 II. An installation directory C: \Program Files\Foxy
II. An installation directory C: \Program Files\Foxy