Skip to Content
- Home
- About
- Services
-
Top Asked
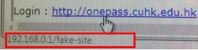
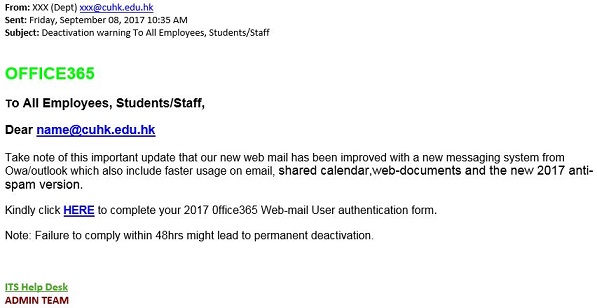
- Change OnePass Password
- Forgot Password
- Enrol in Duo 2FA for new users
- Transfer Duo 2FA to my new phone
- Collect New Staff Account
- Collect New Student Account
- Microsoft Copilot for the Web
- Define Email Address (via Campus Network or CUHK VPN)
- Manage Project / Other Account(s) (via Campus Network or CUHK VPN)
-
News
- System Maintenance of CUPIS from 12 Jul 2025 12am – 13 Jul 2025 10am
- Users may be intermittently unable to access their mailboxes in Exchange Online using any connection method
- (Resumed) Users may be unable to see free and busy information for other users within their organization through Outlook
- WiFi / ResNet / VPN Authentication Service Maintenance on 2 – 5 Jul
- Summer Opening Hours of User Areas from 30 Jun to 24 Aug
- Contact