Ransomware Variants: “Petya”
The latest ransomware outbreak “Petya” is attacking companies across the globe today, the new variants of ransomware are also known as Petwrap / Petya / NotPetya / Nyetya. Quite a number of companies in Europe and Asia are reporting affected.
From the initial analysis, same as last time ransomware outbreak “WannaCry”, this ransom uses multiple techniques to spread, including one which was addressed by a Windows vulnerability MS17-010 via SMBv1. it was also reported that the ransomware used phishing email to spread. once infected, the machine will spread via local network before it encrypts data on local machine.
Systems Affected
All versions of Windows Servers and Clients.
Impact
Petya ransomware modifies the master boot records (MBR) and encrypts the Master File Table (MFT) of infected Windows computers, making affected machines unusable.
- Modify the MBR and encrypt MFT on victims’ computers.
- Infected system will reboot after an hour. Since the MBR has been damaged, the system will display a ransom note instead of booting properly.
- Data will be unrecoverable due to encrypted by ransomware.
- Spread itself to other computers in the local network.
Until now, there is NO effective method to decrypt all the kidnapped files.
Actions Preventing Petya Attack
Firewall
- Enable your firewalls as well as intrusion detection and prevention systems.
- Ensure latest signature has been applied on IPS.
- Proactively monitor and validate the incoming and outgoing traffic of the network.
Windows Client
- Ensure PC has up-to-date Windows updates, especially MS17-010.
- Disable SMBv1 – https://support.microsoft.com/en-us/help/2696547/how-to-enable-and-disable-smbv1-smbv2-and-smbv3-in-windows-and-windows
- Ensure up-to-date anti-virus signatures from your anti-virus software such as Kaspersky or Windows Defender updated.
- Backup your files regularly and keep them in a separate and safe place.
- Do not open email/attachments from unknown/untrusted source
- Ensure you have a “strong” system password
Windows Server
- Same as Windows Client.
- Block incoming traffic to Port 445 in Windows Firewall if no SMB service is needed.
Note: these are good security defense-in-depth recommendations for prevention of being infected, but these steps alone do not guarantee against infection.
As a Victim:
Since Petya will start data encryption after system reboot, if user found their Windows hang suddenly and reboot (like the screen below), they should:
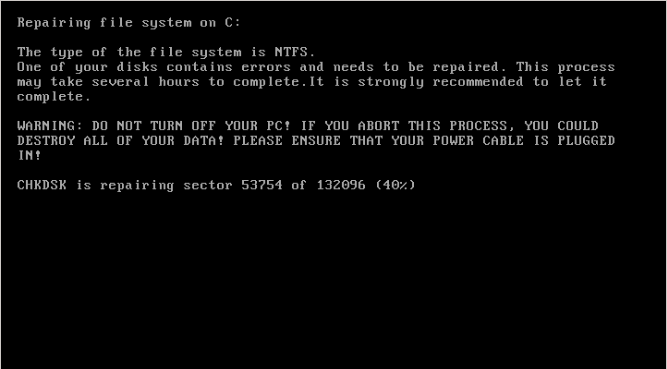
- Turn off the computer IMMEDIATELY once the Windows Logo appears. Otherwise, the encryption process will be started.
- Then, use the Live CD to boot the system, or unplug the hard disk and connect it to other computer for cleanup/create Kill-Switch and data backup.
- DO NOT respond to any kidnapper by attempting payment and instead to report the incident to ITSC and the Police.
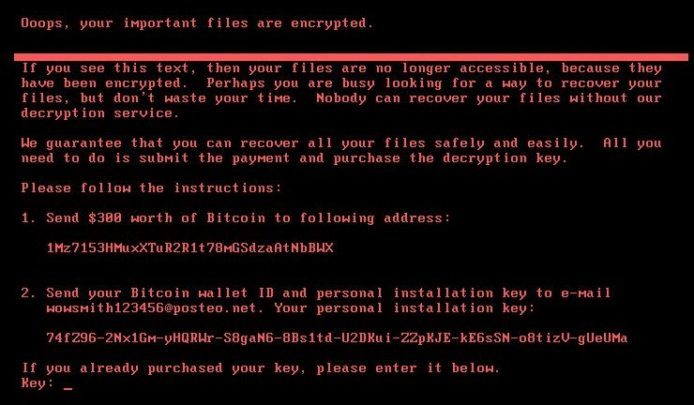
Note : Once the encryption process is completed, the data will be unrecoverable.
Reference:
- HKCERT Security Bulletin:
Petwrap / NotPetya Ransomware Encrypts Victim Data - US-CERT:
Multiple Petya Ransomware Infections Reported - Microsoft Security Bulletin MS17-010 – Critical:
https://technet.microsoft.com/en-us/library/security/ms17-010.aspx - Large-Scale Ransomware Attack In Progress, Hits Europe Hard:
http://blog.trendmicro.com/trendlabs-security-intelligence/large-scale-ransomware-attack-progress-hits-europe-hard/ - Recent News:
http://www.bbc.com/news/technology-40416611
https://unwire.hk/2017/06/28/petya/top-news/#!prettyPhoto - Indicators of Compromise:
https://securingtomorrow.mcafee.com/mcafee-labs/new-variant-petya-ransomware-spreading-like-wildfire/ - Other Ransomware Variants
Please visit here for more Information Security tips.
Created on: 28 Jun 2017